Authentication over Insecure Wireless Channels

This project deals with message authentication and integrity protection in wireless networks. The main focus of this project is authentication without pre-shared keys and/or credentials. Three proposals have so far emerged in this context: INTEGRITY-CODING, INTEGRITY-REGIONS and reliance on SHORT STRING COMPARISON. Particular attention in this project was devoted to authentication through presence awareness (i-codes and i-regions).
We proposed or contributed to the following proposals for authentication over insecure wireless channels and analyzed the underlying conditions; further information and related publications are given below:
Signal and Message Manipulations: Investigation of signal and message manipulations on the wireless channel
Integrity codes: Message Integrity Protection and Authentication Over Insecure Channels
Integrity regions: Authentication Through Presence in Wireless Networks
Authentication based on short string comparison: A set of simple techniques for key establishment over radio link in peer-to-peer networks
Syssec members on the project:
- Srdjan Capkun
Past and present collaborations:
- external pageProf. Mario Cagaljcall_made (Univ. of Split, Croatia), external pageProf. Jean-Pierre Hubauxcall_made (EPFL, Switzerland), Prof. Mani Srivastava (external pageUCLAcall_made).
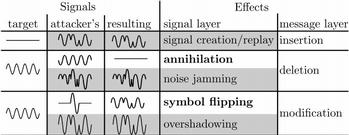
Investigation of Signal and Message Manipulations on the Wireless Channel
This work explores the possibilities of the attacker to tamper with the integrity of messages and signals on the wireless channel.
We explore the suitability of Dolev-Yao-based attacker models for the security analysis of wireless communication. The Dolev-Yao model is commonly used for wireline and wireless networks. It is defined on abstract messages exchanged between entities and includes arbitrary, real-time modification of messages by the attacker. In this work, we aim at understanding and evaluating the conditions under which these real-time, covert low-energy signal modifications can be successful. In particular, we focus on the following signal and message manipulation techniques: symbol flipping and signal annihilation. We analyze these techniques theoretically, by simulations, and experiments and show their feasibility for particular wireless channels and scenarios.
Related publication:
- Christina Pöpper, Nils Ole Tippenhauer, Boris Danev, Srdjan Capkun
Investigation of Signal and Message Manipulations on the Wireless Channel
In Proceedings of the European Symposium on Research in Computer Security (ESORICS), 2011
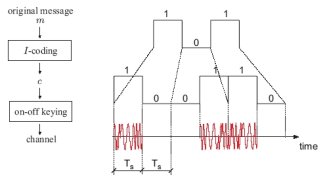
Integrity Codes: Message Integrity Protection and Authentication Over Insecure Channels
Inspired by unidirectional error detecting codes that are used in situations where only one kind of bit errors are possible (e.g., it is possible to change a bit “0” into a bit “1”, but not the contrary), we propose integrity codes (I-codes) for a radio communication channel, which enable integrity protection of messages exchanged between entities that do not hold any mutual authentication material (i.e. public keys or shared secret keys).
The construction of I-codes enables a sender to encode any message such that if its integrity is violated in transmission over a radio channel, the receiver is able to detect it. In order to achieve this, we rely on the physical properties of the radio channel. We analyze in detail the use of I-codes on a radio communication channel and we present their implementation on a Mica2 wireless sensor platform as a “proof of concept”. We finally introduce a novel concept called “authentication through presence” that can be used for several applications, including for key establishment and for broadcast authentication over an insecure radio channel. We perform a detailed analysis of the security of our coding scheme and we show that it is secure with respect to a realistic attacker model.
Related publications and presentations:
- Srdjan Capkun, Mario Cagalj, Ramkumar Rengaswamy, Ilias Tsigkogiannis, Jean-Pierre Hubaux, Mani Srivastava
Integrity Codes: Message Integrity Protection and Authentication Over Insecure Channels
in IEEE Transactions on Dependable and Secure Computing, 2008 [DownloadPDF (PDF, 265 KB)vertical_align_bottom]
- Mario Cagalj*, Srdjan Capkun*, RamKumar Rengaswamy, Ilias Tsigkogiannis, Mani Srivastava and Jean-Pierre Hubaux,
Integrity (I) codes: Message Integrity Protection and Authentication over Insecure Channels,
in Proceeding of the IEEE Symposium on Security and Privacy (S&P), 2006 [DownloadPDF (PDF, 260 KB)vertical_align_bottom] (* equally contributing authors)
Presentation: [DownloadPDF (PDF, 233 KB)vertical_align_bottom]
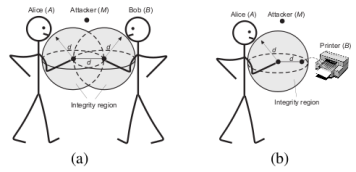
Integrity Regions: Authentication Through Presence in Wireless Networks
We introduce Integrity (I) regions, a novel security primitive that enables message authentication in wireless networks without the use of pre-established or pre-certified keys. Integrity regions are based on the verification of entity proximity through time-of-arrival ranging techniques. We demonstrate how I-regions can be efficiently implemented with ultrasonic ranging, in spite of the fact that ultrasound ranging techniques are vulnerable to distance enlargement and reduction attacks. We further discuss how I-regions can be used in key establishment applications in peer-to-peer wireless networks.
Examples of applications of integrity regions. (a) Key establishment (e.g., exchange of the Diffie-Hellman public keys - bidirectional message au- thentication and integrity verification); (b) Device authentication (user receives an authentic public-key of a device - unidirectional message authentication and integrity verification).
Srdjan Capkun, Mario Cagalj, Ghassan Karame, Nils Ole Tippenhauer
Integrity Regions: Authentication Through Presence in Wireless Networks
IEEE Transactions on Mobile Computing, 2010 [Downloadbibtex (BIB, 314 Bytes)vertical_align_bottom]
Related publications and presentations:
- Srdjan Capkun* and Mario Cagalj*
Integrity Regions: Authentication Through Presence in Wireless Networks
ACM Workshop on Wireless Security, WiSe 2006 [DownloadPDF (PDF, 174 KB)vertical_align_bottom]
(* equally contributing authors)
Authentication Based on Short String Comparison
We present a set of simple techniques for key establishment over a radio link in peer-to-peer networks. Our approach is based on the Diffie-Hellman key agreement protocol, which is known to be vulnerable to the “man-in-the-middle” attack if the two users involved in the protocol do not share any authenticated information about each other (e.g., public keys, certificates, passwords, shared keys, etc.) prior to the protocol execution. In this paper, we solve the problem by leveraging on the natural ability of users to authenticate each other by visual and verbal contact. We propose three techniques. The first is based on visual comparison of short strings, the second on distance bounding, and the third on integrity codes; in each case, the users do not need to enter any password or other data, nor do they need physical or infrared connectivity between their devices. We base our analysis on a well-established methodology that leads us to a rigorous modularization and a thorough robustness proof of our proposal.
Related publications and presentations:
- M. Cagalj, S. Capkun, J. P. Hubaux,
Key agreement in peer-to-peer wireless networks,
Proceedings of the IEEE (Special Issue on Cryptography and Security), 2006 [DownloadPDF (PDF, 456 KB)vertical_align_bottom]
