Security of Medical Devices
We made the following proposals for securing medical devices; further information and related publications are given below:
Proximity-Based Access Control for Implantable Medical Devices: We propose a proximity-based access control scheme for implantable medical devices (IMDs).
On Limitations of Friendly Jammin gofr Confidentiality: We construct a MIMO-based attack that allows the attacker to recover data protected by friendly jamming and refine the conditions for which this attack is most effective.
Enabling Trusted Scheduling in Embedded Systems: We propose an embedded system architecture that can guarantee the on-schedule execution of critical applications despite other parts of the system being compromised.
Syssec members on the project:
- Kasper Bonne Rasmussen, Thomas Heydt-Benjamin, Srdjan Capkun
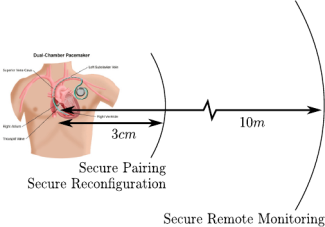
Proximity-Based Access Control for Implantable Medical Devices
We propose a proximity-based access control scheme for implantable medical devices (IMDs). Our scheme is based on ultrasonic distance bounding and enables an implanted medical device to grant access to its resources only to those devices that are in its close proximity. We demonstrate the feasibility of our approach through tests in an emulated patient environment. We show that, although implanted, IMDs can successfully verify the proximity of other devices with high accuracy. We propose a set of protocols that support our scheme, analyze their security in detail and discuss possible extensions. We make new observations about the security of implementations of ultrasonic distance-bounding protocols. Finally, we discuss the integration of our scheme with existing IMD devices and with their existing security measures.
Related publication:
- Kasper Bonne Rasmussen, Claude Castelluccia, Thomas S. Heydt-Benjamin and Srdjan Capkun
Proximity-based Access Control for Implantable Medical Devices
In Proceedings of the ACM Conference on Computer and Communications Security (CCS), 2009 [DownloadPDF (PDF, 470 KB)vertical_align_bottom | Downloadbibtex (BIB, 399 Bytes)vertical_align_bottom]
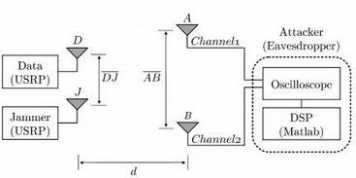
On Limitation of Friendly Jamming for Confidentiality
Wireless communication provides unique security challenges, but also enables novel ways to defend against attacks. In the past few years, a number of works discussed the use of friendly jamming to protect the confidentiality of the communicated data as well as to enable message authentication and access control. In this work, we analytically and experimentally evaluate the confidentiality that can be achieved by the use of friendly jamming, given an attacker with multiple receiving antennas. We construct a MIMO-based attack that allows the attacker to recover data protected by friendly jamming and refine the conditions for which this attack is most effective. Our attack shows that friendly jamming cannot provide strong confidentiality guarantees in all settings. We further test our attack in a setting where friendly jamming is used to protect the communication to medical implants.
Related Publication:
Nils Ole Tippenhauer, Luka Malisa, Aanjhan Ranganathan, Srdjan Capkun
On Limitations of Friendly Jamming for Confidentiality
In Proceedings of the IEEE Symposium on Security and Privacy (S&P), 2013 [DownloadPDF (PDF, 1.4 MB)vertical_align_bottom]
Other project publications:
- Daniel Bodmer, Srdjan Capkun
On the Security and Privacy in Cochlear Implants
ETH Zurich, D-INFK, Technical Report No. 677, 2010 [DownloadPDF (PDF, 57 KB)vertical_align_bottom]
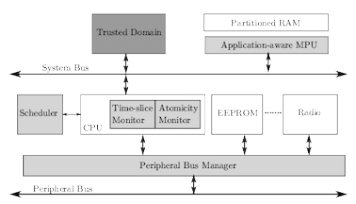
Enabling Trusted Scheduling in Embedded Systems
The growing complexity and increased networking of security- and safety-critical systems expose them to the risk of adversarial compromise through remote attacks. These attacks can result in full system compromise, but often the attacker gains control only over some system components (e.g., a peripheral) and over some applications running on the system. We consider the latter scenario and focus on enabling on-schedule execution of critical applications that are running on a partially compromised system - we call this trusted scheduling. We identify the essential properties needed for the realization of a trusted scheduling system and we design an embedded system that achieves these properties. We show that our system protects not only against misbehaving applications but also against attacks by compromised peripherals.
Related publication:
Ramya Jayaram Masti, Claudio Marforio, Aanjhan Ranganathan, Aurélien Francillon, and Srdjan Capkun
Enabling Trusted Scheduling in Embedded Systems
In Proceedings of 28th Annual Computer Security Applications Conference (ACSAC), 2012 [DownloadPDF (PDF, 404 KB)vertical_align_bottom]

